Follow these 3 Steps to protect yourself!
Today I almost clicked on an email that was most definitely a spam/scam message. The email looked that legit to me (and I definitely should know better). Only after taking a few seconds and remembering these three easy steps did I catch myself before it was too late.
First some vital information: Many of the spam emails you receive are sent for one reason, to get you to click on any of the links contained in the email. Once you click on a link, your web browser will open and there is a good chance your browser/computer could be infected with a virus or some sort of malware. But there is more… You could be sent to a website that looks JUST like a real company’s site, and once there, you may innocently proceed to type in your user-name and password to login to your account.
But Guess what?
You just gave your real account information directly to a hacker.
The site you were sent to was in fact a bogus website, and when you logged into your account, you sent your information off to the hacker. What is even more frightening is that some hackers are so skilled, they can grab your real user-name and password you just typed, save that information to their own computers, then incredibly, log you into the legitimate company’s website! (all within a second or two)
Now you are truly logged into www.Amazon.com, BUT you gave away your user-name and password information to the hacker, and you don’t even know you did so!
So before we even get to these 3 quick steps, know that the goal of most spam email is to get you to “click”. That means whatever you do, do NOT click unless you are VERY sure about the email message; even if the email appears to come from someone you know (or a company you trust, like Amazon, the example shown below).
Now without further delay, here are your three quick steps:
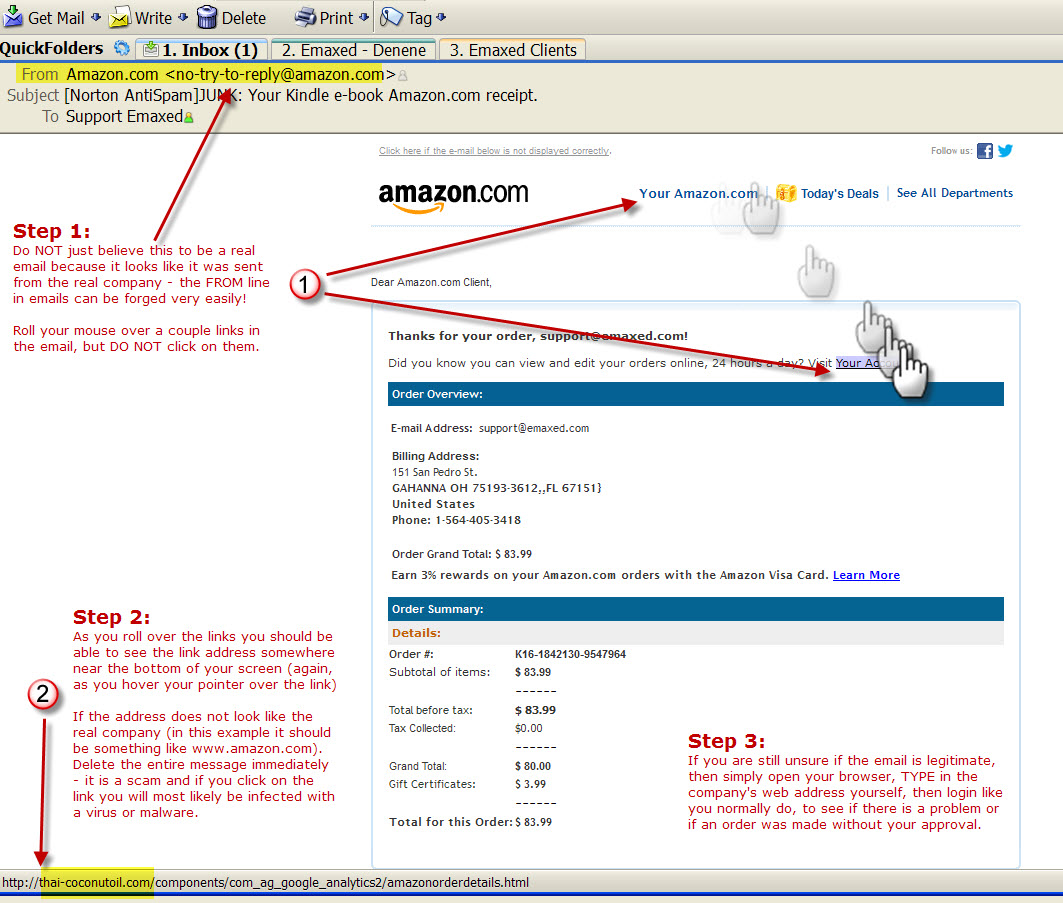
Step 1:
Roll your mouse over any link in the suspected email message.
Step 2:
At the bottom of your email window, you “should” see the URL address (the website) that link represents. If the URL does NOT contain the main company web address that seems to have sent this email, do NOT click on any of the links in the email. For instance, the example here appears to have been sent by Amazon, stating that I placed an order – which of course I did not place. The plan is to get me excited and worried enough to want to immediately find out if someone broke into my account, by clicking on a link. **
Step 3:
If you are still worried that someone has broken into your account. Simply open up your browser, type in the company (www.amazon.com) and login to your account like you always do. Then look up your orders.
In fire rescue they say; Stop, Drop and Roll…
With email rescue let’s say; Stop, Think, and DON’T CLICK
** If your email reader does not display the URL at the bottom of your screen, then you can try right-clicking the link (which will NOT open your browser but will open a small pop-up menu). From that menu choose “copy link location” and then right-click into a word processing program and choose to “paste”. That will show you the link’s URL without it opening up your browser.

 Pamela Slaton is by far one of our most interesting clients as she is known as a miracle worker by the nearly 3,000 adoptees she’s helped. After founding her own practice and using a never-quit policy to get around restrictive state laws, she has been able to locate 90% of her clients’ missing relatives, and has earned a reputation as one of the country’s leading investigative genealogists. She helped DMC find his birth parents on Vh1’s Emmy-Award-winning documentary My Adoption Journey, and now facilitates powerful reunions from start to finish on her Oprah Winfrey Network show.
Pamela Slaton is by far one of our most interesting clients as she is known as a miracle worker by the nearly 3,000 adoptees she’s helped. After founding her own practice and using a never-quit policy to get around restrictive state laws, she has been able to locate 90% of her clients’ missing relatives, and has earned a reputation as one of the country’s leading investigative genealogists. She helped DMC find his birth parents on Vh1’s Emmy-Award-winning documentary My Adoption Journey, and now facilitates powerful reunions from start to finish on her Oprah Winfrey Network show. Back in college, one class that seemed to inspire an instant feeling of dread was Statistics 101. Simply mentioning the class would bring the strongest business students to their knees! Not to mention after the first few exams, the phrase “why do we need this {expletive} class anyway, no one uses this stuff in the real world?” could be heard throughout the business department.
Back in college, one class that seemed to inspire an instant feeling of dread was Statistics 101. Simply mentioning the class would bring the strongest business students to their knees! Not to mention after the first few exams, the phrase “why do we need this {expletive} class anyway, no one uses this stuff in the real world?” could be heard throughout the business department.



